1. Transparency at cost
Blockchain technology revolutionized digital transactions through its fundamental principle of transparency - every transaction is visible and verifiable on the public ledger. However, this transparency creates a significant paradox: while it ensures trust and verification, it simultaneously compromises user privacy and creates vulnerabilities that malicious actors can exploit.
The first major challenge lies in the lack of confidentiality. Although blockchain transactions are pseudonymous, advanced analytics tools can easily trace transactions, potentially revealing participant identities [1]. This missing confidentiality makes blockchain interactions exploitable and leaves users vulnerable to risks, including frontrunning and leakage of private information. Such privacy concerns create a substantial barrier to widespread adoption, particularly for enterprises and consumers who require confidentiality in their financial dealings.
The second major challenge emerges from how blockchains order transactions. Block proposers have full control over which transactions to include and how to order them, leading to what is called Maximal Extractable Value (MEV). MEV is the maximum value that can be extracted from a proposed block by arranging and sequencing transactions. To maximize the additional value within a block, the block proposers strategically place their own transactions to enhance their profitability. [2] This rearrangement of transactions results in unexpected outcomes for the user. ****Since the outcome is different than what user expected, these MEV actions are called "MEV Attacks" or a “silent tax”. Below are the possible attacks that could happen:
- Backrunning: A profitable arbitrage opportunity is detected and a trade is inserted immediately after a large transaction.
- Frontrunning: A higher gas transaction is submitted before the original user's swap to profit from the price movement.
- Sandwich Attacks: Transactions are placed before and after a user's swap, causing intentional slippage and extracting profits.
Ultimately, MEV creates an unfair trading environment, where users pay hidden costs while block proposers extract profits.
2. PRISM & Encrypted Intents: Protecting Transactions through Fully Homomorphic Encryption
To address these fundamental challenges of confidentiality and MEV exploitation, Fluton introduces a Privacy-Preserving Intent Settlement Mechanism (PRISM) leveraging encrypted intents. Encrypted intents enable privacy-preserving, MEV-resistant transactions by encrypting a user intent until execution (read more on intents in Union’s Intents Bridging article [3]). This is achieved through Fully Homomorphic Encryption (FHE), a technology that enables processing encrypted data without decrypting it [4]. This means with FHE, we are able to perform mathematical operations, such as addition and subtraction, over encrypted data without knowing what the actual data is.
There are two primary types of encrypted intents:
Semi-confidential encrypted intents
If you just want to protect your transaction from MEV attacks and don't care about privacy that much, semi-confidential encrypted intents would be your most optimal choice. To prevent MEV, encrypting the amount you're swapping is sufficient and you don't have to pay more gas for encrypting other details.
Fully-confidential encrypted intents
If you care about privacy and you want to hide other details such as the token address or the target network, you can use fully-confidential encrypted intents (though this option will increase gas costs). Please note that the protocol does not support masking receiver addresses on the target chain, as this would enable untraceable transactions and thereby pose regulatory challenges. However, this does not mean that transaction confidentiality is entirely lost. The key distinction lies in what information remains hidden and what remains visible. Even though receiver addresses are public on-chain, the intent details such as the target network and the amount are encrypted until execution. This ensures that third parties cannot front-run, manipulate, or extract value and information from the transaction.
2.1 PRISM: A Privacy-Preserving Intent Settlement Mechanism
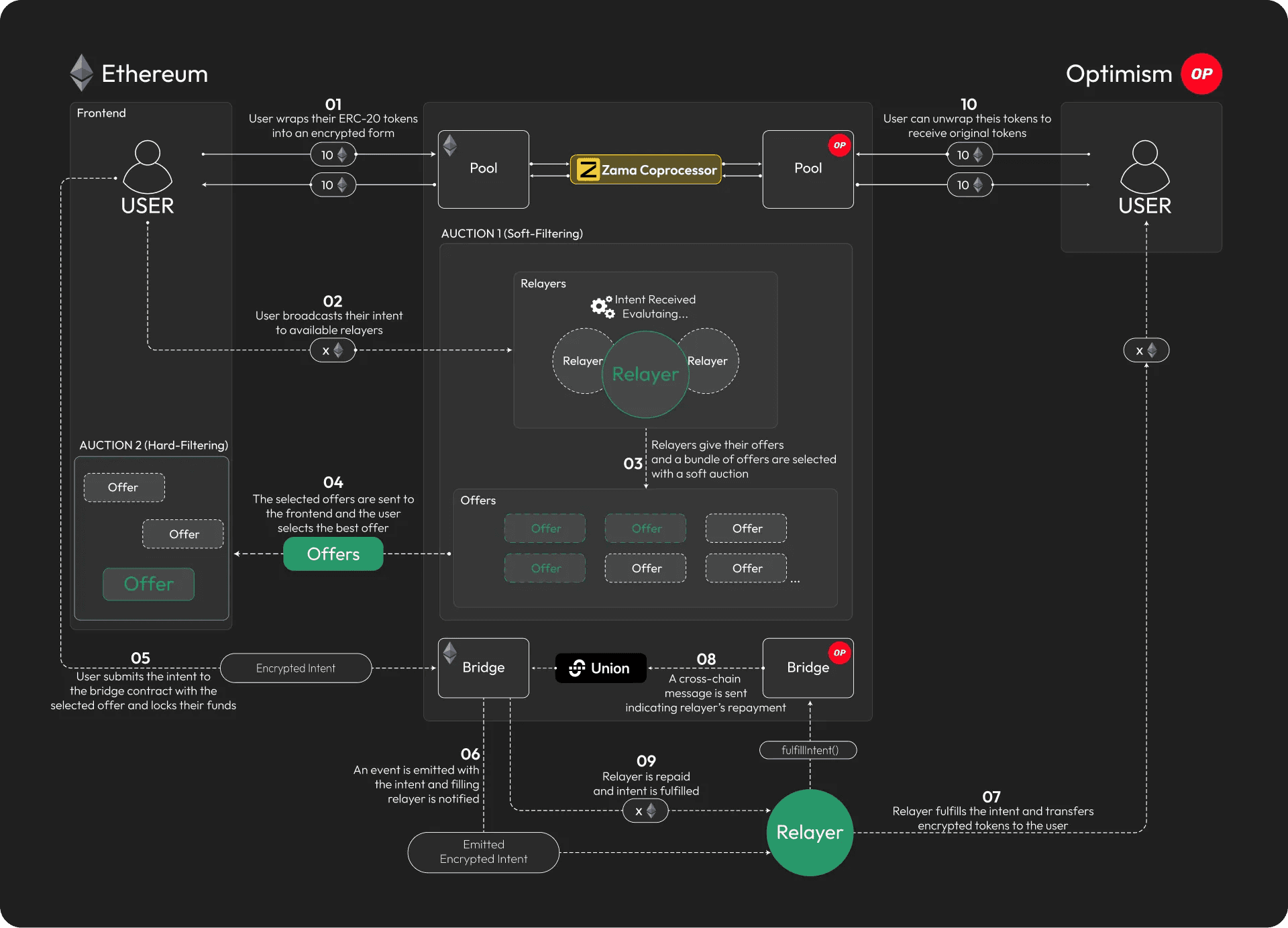
architecture
- User Defines an Intent: A user specifies an action (e.g., bridge 10 ETH from Ethereum to Optimism). The intent is encrypted using FHE, making it unreadable to the network.
- Solvers Receive the Encrypted Intent and Submit their Offer: The encrypted intent is broadcasted to the solvers. Since the intent remains encrypted, no one can frontrun, censor, or manipulate it. The solvers give their offers to the user blindly. The offers usually look like this: “I'll take 1% fee from the amount you're sending but I'm waiting the transaction to be finalized.”, or “I'll take 2% fee + 1$ base fee but I won't wait for finality.”
- User Chooses an Offer and Authorizes the Relayer: The user chooses the best offer whatever they're prioritizing, whether it's lower fees or faster execution. Then they authorize a relayer to fulfill their intent. The solver executes the transaction as specified without decrypting the details, ensuring fairness and privacy.
- Cross-Chain Settlement: If the transaction involves bridging, encrypted messages coordinate execution across different chains via Union's cross-chain messaging infrastructure.
Below, you’ll see an example bridge function from Fluton’s FHE enabled smart contract:
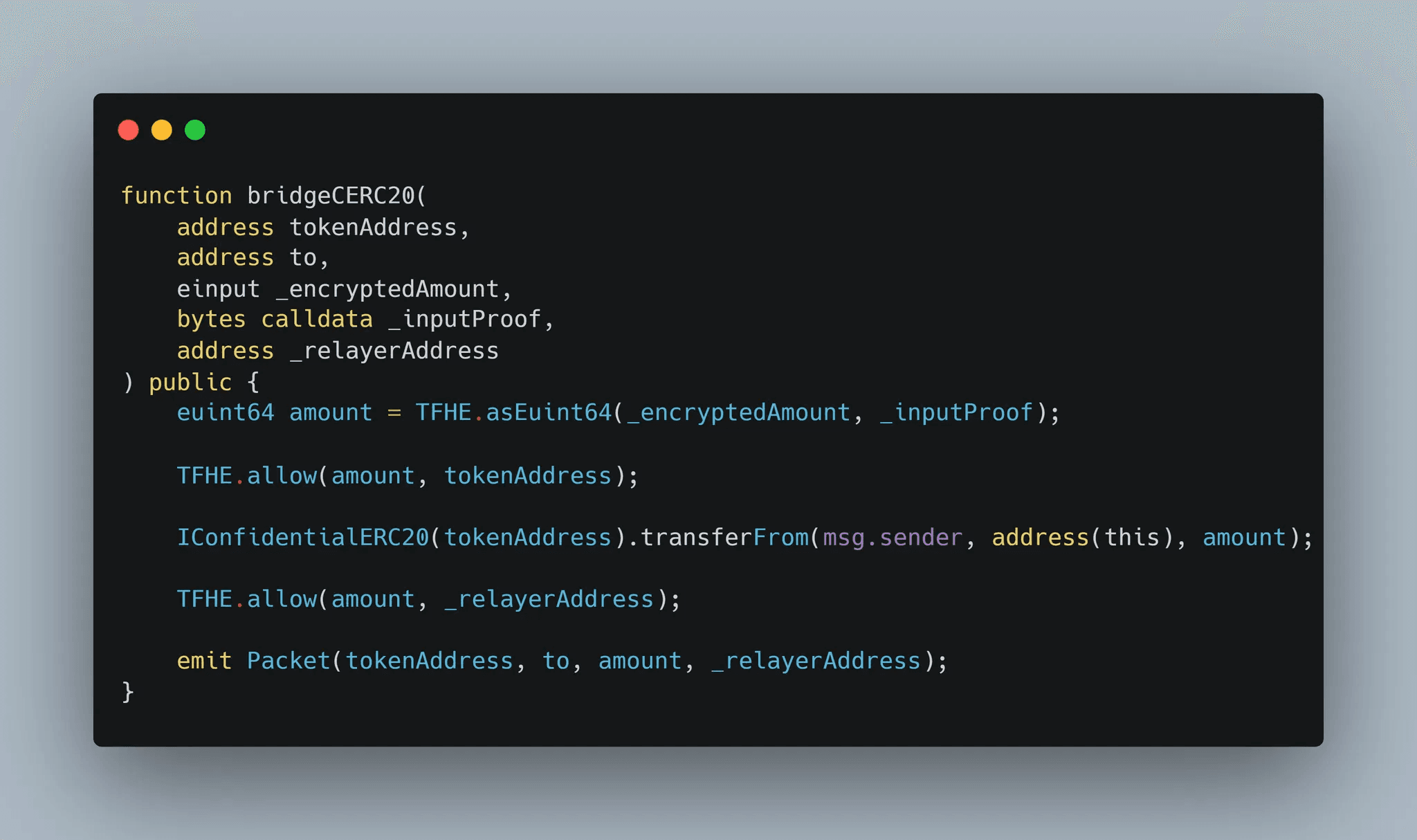
Alternative code base
3. Conclusion
Fluton's Privacy-Preserving Intent Settlement Mechanism (PRISM) directly addresses two key blockchain challenges: lack of confidentiality and MEV exploitation. By leveraging Fully Homomorphic Encryption, PRISM enables encrypted intents that keep transaction details encrypted until execution, preventing MEV attacks while ensuring regulatory compliance. This enhances user privacy, fosters a fairer trading environment, and lowers adoption barriers for both enterprises and individuals. Through integration with Union's cross-chain messaging infrastructure, encrypted intents demonstrate how privacy-preserving technology can operate across multiple blockchain networks while maintaining both security and functionality.
Next up, Fluton is actively exploring leveraging Hooks and AI agents to enhance user experience. Hooks will enable automated post-transaction actions, allowing users to define multi-step operations like cross-chain transfers followed by automatic staking. For example,
I want to send 100 USDC from Optimism to Base, and once my funds arrive, I want to stake them in the highest-yield staking pool available.
Furthermore, users should be able to interact with an AI agent designed to simplify DeFi transactions - instead of manually navigating through the interface. This assistant should understand the user's intent, determine the most optimal route, and execute the process accordingly.